The issue with VDM30in30 is you really have to plan out what you are going to blog about for 30 days. Then you have to assume that someone is going to read it and need to make sense of it.
I watched my stats for last year and my weekday posts had significant uptick in viewership but the weekend posts went largely ignored. So this time around I wanted to try something different and post about a non-technology subject on the weekends. This year I am not doing a large number of posts upfront and scheduling them instead I am writing them each the night or day before they need to go live. This adds some stress to be sure but hopefully not too much.
Saturdays for me are about time with my wife and kids and mostly about soccer during 3 out of 4 seasons of the year. As some of you know I coach 2 soccer teams a U13 and a U8 team for my daughter and son. I have played soccer my entire life and love the game. As the sport has grown in popularity I see more and more in the IT world talking about it and asking for drills for their kids.
So I figured this weekend we could take some time to talk soccer coaching! Today’s topic Offense:
It’s important when teaching young players to explain how a field is laid out. I start by describing how we divide a soccer field or pitch into 3rds horizontally. The defensive, midfield, and attacking 3rds.
The Defensive 3rd is where we want to clear the ball away from our goal, the midfield 3rd is the toughest area of the field and is important to win the ball and use controlled passing, the attacking third is all about playing the ball into the box and centering for shots on goal.
For young kids they all want to chase a ball around the field especially at U6-U9. To get them away from the herd mentality it’s good to explain the soccer field with the 3rds and then carve it up again for them vertically. With each wing zone being a 3rd and then a center 3rd for the striker.
Kids understand zones or bases from playing tag so reinforcing that message is easy when using fun drills like wall passing or just cross and shoot with 3 offensive players. Here are some of my favorites.
http://www.soccerxpert.com/soccerdrills/id1213.aspx
http://www.soccerxpert.com/soccerdrills/id1209.aspx
Something that coaches always ask and parents as well is how to work on aggressiveness. “My kid just doesn’t want to get after the ball”, or “they aren’t attacking enough”. Believe me if I had a cure for that I would be the greatest youth coach of all time. The answer is it comes to each kid in their own time. Sometimes it never comes because they are super sweet kids and overly kind (aka my daughter most games). But if you are coaching and need to get the kids to attack on offense more and challenge the ball. I love the 50/50 challenge there is a link below but essentially it’s two lines on either side of the goal 3 ft off the end line. The coach tosses the ball over the goal out onto the field the first two players in line charge out win the ball and each tries to score, an steal the ball from the other player. Play ends with a goal or out of bounds ball is played.
http://www.soccerxpert.com/soccerdrills/1v1-to-goal-team-competition.aspx
Finally a drill I run a lot is the run and cross. I believe firmly that youth soccer should play inside out to outside in. That means you never play a ball into the middle of your own goal always play out to the sidelines, and take the open sidelines to the corner in the attacking 3rd to play the ball into the box where the striker and far wing are waiting. I do this drill until players hate it but honestly its one of the best to teach soccer the way it’s meant to be played on the attack.
So let me know what you think about a non-tech post and if you have some favorite drills for your kids I am all ears.

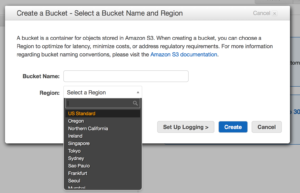
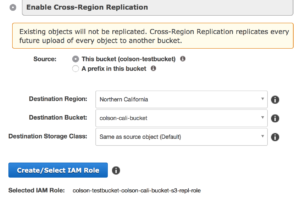 But it can also be tied to cross region replication meaning your data can be replicated closer to the point of utilization or simply for disaster recovery purposes.
But it can also be tied to cross region replication meaning your data can be replicated closer to the point of utilization or simply for disaster recovery purposes.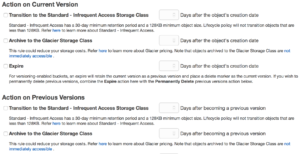 global so make it unique. Permission to buckets are handled via IAM and applied at the bucket level. You can put permissions on objects but if you have more restrictive permissions at the bucket level they will trump whatever you have at the object. S3 has some really great features as well, like logging to track object access, versioning which flags files at change and allows you to roll back to older copies, and lifecycle management. Lifecycle management lets you move objects across classes of S3 storage and even into Glacier which is AWS’ archival storage service, we will get to that in a moment.
global so make it unique. Permission to buckets are handled via IAM and applied at the bucket level. You can put permissions on objects but if you have more restrictive permissions at the bucket level they will trump whatever you have at the object. S3 has some really great features as well, like logging to track object access, versioning which flags files at change and allows you to roll back to older copies, and lifecycle management. Lifecycle management lets you move objects across classes of S3 storage and even into Glacier which is AWS’ archival storage service, we will get to that in a moment. There is a lot that can be said here about Storage Gateway, this is one of the first on-prem offerings from AWS. Storage Gateway is deployed in your datacenter as either a Hyper-V or VMware VM. You get 3 options for configuration cached volume mode where the most used data has a local copy saving on data transfer rates. Stored volume mode this is where storage gateway is the local volume store and asynchronously backs up data to S3 via point in time snapshots. The last option is Virtual Tape Library (VTL) mode this will allow you to use your backup software to treat the storage gateway as a tape library storing data direct to S3 or to a Virtual Tape Shelf (VTS) backed by Glacier which looks like a standard iSCSI connection.
There is a lot that can be said here about Storage Gateway, this is one of the first on-prem offerings from AWS. Storage Gateway is deployed in your datacenter as either a Hyper-V or VMware VM. You get 3 options for configuration cached volume mode where the most used data has a local copy saving on data transfer rates. Stored volume mode this is where storage gateway is the local volume store and asynchronously backs up data to S3 via point in time snapshots. The last option is Virtual Tape Library (VTL) mode this will allow you to use your backup software to treat the storage gateway as a tape library storing data direct to S3 or to a Virtual Tape Shelf (VTS) backed by Glacier which looks like a standard iSCSI connection. I would be remised if I didn’t mention what Snowball is, imagine a world in which physics didn’t
I would be remised if I didn’t mention what Snowball is, imagine a world in which physics didn’t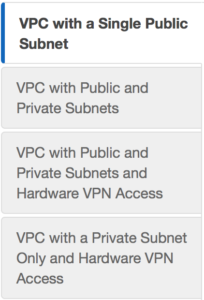 We can do a custom build, but the AWS console has a sweet little VPC wizard we can use. Let’s use the Wizard cause why not. So as you can see you have 4 options. We are going to select Option 2: a VPC with one public and one private subnet.
We can do a custom build, but the AWS console has a sweet little VPC wizard we can use. Let’s use the Wizard cause why not. So as you can see you have 4 options. We are going to select Option 2: a VPC with one public and one private subnet.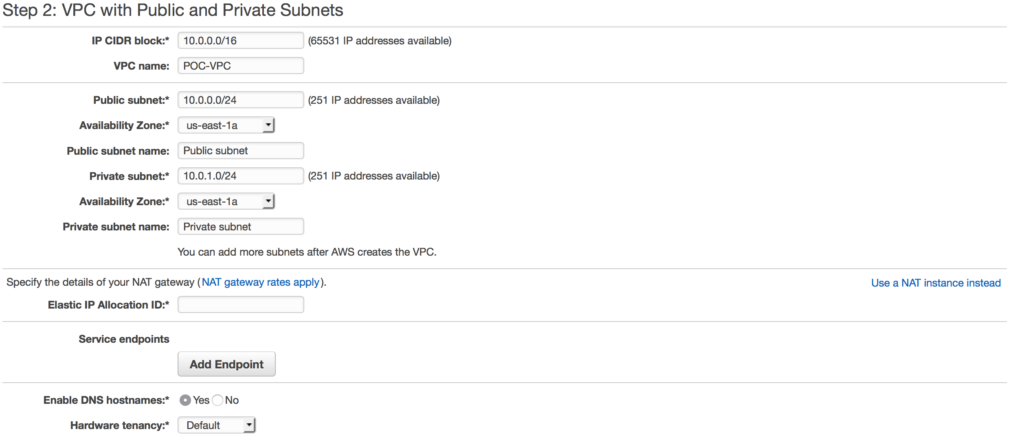 in this case I am choosing a NAT gateway instead of a NAT instance. There are several reasons to choose one over another, one of the main differences is a NAT gateway will auto-scale whereas a NAT instance
in this case I am choosing a NAT gateway instead of a NAT instance. There are several reasons to choose one over another, one of the main differences is a NAT gateway will auto-scale whereas a NAT instance 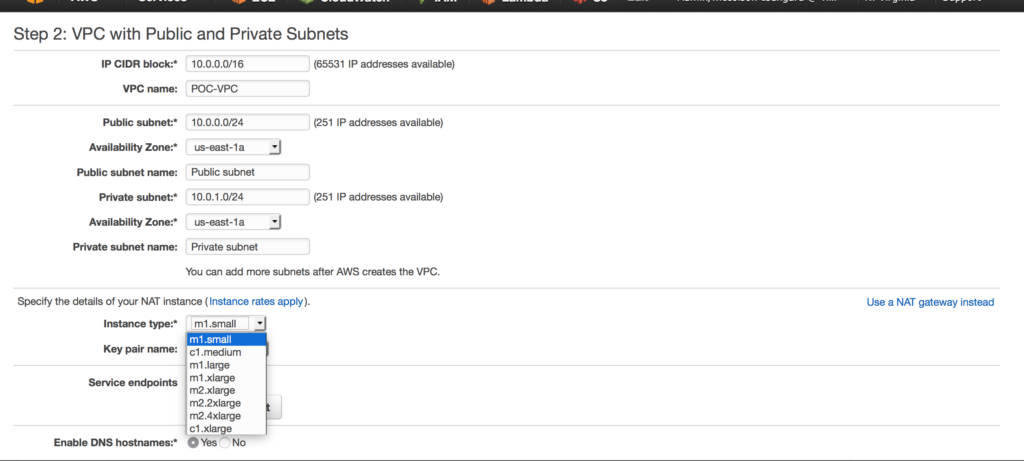 requires a script for failover. Compare your options
requires a script for failover. Compare your options 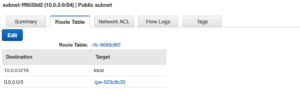 By using the VPC wizard once it’s completed it’s set up our public subnet is also assigned an internet gateway. This means we now have external connectivity to our public subnet.
By using the VPC wizard once it’s completed it’s set up our public subnet is also assigned an internet gateway. This means we now have external connectivity to our public subnet.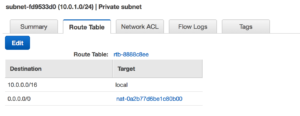 With that same setup the Private subnet is behind the NAT. We are ready to start building out our EC2 instances.
With that same setup the Private subnet is behind the NAT. We are ready to start building out our EC2 instances.