In our first post for VDM30in30 we touched on AWS terminology, today we are going to get into IAM since it is at the root of your AWS management. When you first create an AWS account you will set up the root account. It is imperative you lock this account down, for realzies this is not the account you want to use to do your day to day administration or to hand out to other users. It’s best practice to enable multi-factor authentication (MFA) on the root account there are several MFA options you can use find out more here.
IAM allows you to create users but wait there’s more, it also is the service that manages roles and access policies for users and service accounts. It’s also the spot where you perform your key creation for encryption, and tie in other Identity Providers like Active Directory. 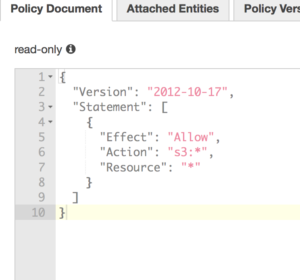
Policies set access levels to resources. There are predefined policies, you can use policy generator which allows you to select from a list or you can create your own policy from scratch via JSON.
Roles are assigned to users and used to assume policies. You can audit a role and it’s underlying policy and determine which policies are actually being used, which allows for a security practice of least privilege to be applied. That’s something we talk about in the world of on-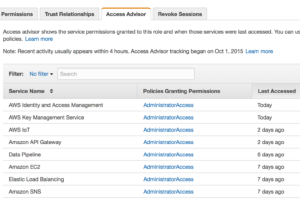 prem administration that is very rarely followed or implemented easily. Here it is just a click of a tab away and an administrator can see what is actually being accessed and make a determination if that role should be limited even further.
prem administration that is very rarely followed or implemented easily. Here it is just a click of a tab away and an administrator can see what is actually being accessed and make a determination if that role should be limited even further.
So that’s a quick and dirty on IAM, Roles and Policies. Stay tuned for the next #VDM30in30 post tomorrow. Hopefully this is useful to someone other than just my mind dump.
