Initially I had hoped that this would be a comparison between VMware’s vRealize Air Compliance (vRAC) and Amazon’s AWS Inspector, unfortunately I wasn’t able to get an in depth meeting with AWS inspector team. So hopefully I will be able to follow this up later with the comparison.
At VMworld 2015 VMware announced vRAC a SaaS service for your cloud compliance. When I first heard about this offering I was excited, because this could mean compliance as a service for any cloud environment you built out which would have some pre-configured packages for HIPPA, FedRamp, PCI, etc.
Obviously I was a little overly wishful, but not to worry because what is there is good enough for a solid start. If like me you thought that vRAC was built on the back of VMware’s Configuration Manager (vCM) we were both wrong. vRAC was built from the ground up as a SaaS offering.
At GA release vRAC will come with networking and security best practices for compliance. PCI and HIPPA will be the first external standards outside of the VMware best practices. vCloud Air has undergone SOC 1, 2, & 3, ISO\IEC 27001, and CSA compliance, additionally use of this product can help organizations meet their compliance requirements by ensuring .
vRAC is not just a vCloud Air offering but can also have a connector deployed as a virtual appliance for an on-prem compliance checker. Currently vCloud Air isn’t considered a tenant for vCloud Air, which means when you build out your vCloud Air tenant environment you need to include a vCenter or extend your network to ensure it is covered by the virtual appliance. The service registers as a vCenter extension service.
There is a 1:1 mapping of the vRAC vApp and a vCenter, but you can do multiple vApps to a SaaS instance. All change streams from the vCenter Orchestrator service are logged and compliance baseline changes are flagged and notifications are sent to the compliance admin. Think of the change stream that is shown at the bottom of your vCenter, showing every snapshot, vm creation along with which user kicked off the task.
If all of this sounds good, maybe I should lay out a couple of limitations. FIrst at GA there is a 40,000 object limit, that includes, VM’s, Hosts, Network instances whatever. At go live there will not be vRA integration, but it is planned and in the works. Federal STIG compliance and OS level compliance are also not planned for day 1. vRealize Operations is also on the roadmap not part of day 1 GA.
vRAC is sold as a subscription service, you manage it via your myVMware subscription services. If this sounds like something for you, you can do an eval and check it out. I found it was easy to install and configure, if not somewhat underwhelming right now or my environment isn’t complex enough, but it’s a good start. Tracking compliance is a difficult and complex task, VMware is trying to make it a little bit easier.
If you are interested in pricing you can find that information here.
Now for you security and compliance nerds out there you should know that vRAC uses OVAL (Open Vulnerability Assessment Language) to integrate solutions and maintain reporting standards. The facilities that house the SaaS service meets industry best practices for physical and network security, some more questions are answered in the official FAQ. To the best of VMware’s ability all data in their care is secured, the network path to the service is a secured VPN connection, and controls are set by the tenant administrator for access. All monitoring is done in real-time, with actionable data with-in 15 minutes of vApp deployment. The vRAC solution is limited to only VMware environments, but this tool is going to have some legs. Check it out and let me know what you think.
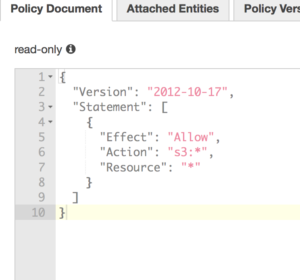
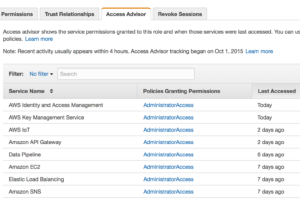 prem administration that is very rarely followed or implemented easily. Here it is just a click of a tab away and an administrator can see what is actually being accessed and make a determination if that role should be limited even further.
prem administration that is very rarely followed or implemented easily. Here it is just a click of a tab away and an administrator can see what is actually being accessed and make a determination if that role should be limited even further.