Shhh listen … no no stop talking and just listen. 
…
…
That’s the sound of a blog too long silenced being reawakened with a new and invigorated passion.
My focus has shifted from that of the world of virtualization to that of the world of cloud first. It truly feels like such a natural part of the evolution of technology and my career. I thought what better time to break out of my silence than with VDM30in30. This year we are going to focus less on the career and ephemeral and try and get into some AWS goodness. Nothing private or NDA will be shared with reInvent so close you can wait. But I want to share what I have learned and what I am doing.
Because language is important, terminology is the first thing we need to tackle so the rest of these posts make sense, I am going to give you a quick and dirty guide to AWS terms and how they map to what you may already know from VMware systems administration.
Region – a region is a geographic boundary that contains multiple availability zones (see availability zone), multiple regions can be used for DR\CooP scenarios beyond a multiple availability zone deployment. Regions are subject to distance & latency from each other.
Availability Zone (AZ) – an availability zone is a single or group of physical facilities that house AWS resources. AZ’s are highly available and low latency within a region. Applications and services can be used within a regions AZs to provide high availability and continuity of operations.
Virtual Private Cloud (VPC) – a VPC is essentially an isolation boundary for a customer’s AWS environment. VPC’s can be peered 1:1 but the communications are not transitive connections must exist in a hub spoke or lollipop design using direct connect. You will have a default VPC when you create your AWS account, don’t use this for your environment create a new VPC we will get into why in another post.
Instances – Instances are the cloud term for VMs and other services being used within the AWS environment. (ie – you are running an EC2 T2 Micro instance, or you have an instance of RDS running in multi-AZ mode)
Security Groups (SGs) – Security Groups are stateful firewalls. That’s really the best way to think of them and will save you headaches later if you wrap your head around this.
Services – Everything in AWS is a service presented by a series of API endpoints anything you can consume in AWS is a service.
EC2 Elastic Cloud Compute – This is the compute\vm environment there are multiple families that we will touch on in a later post
EBS Elastic Block Storage – Block storage for EC2 instances, can be shared across instances, set into RAID groups, snapshotted
S3 Simple Storage Service – Object storage that is HA across all AZ’s in which it is created
Lollipop network – a lollipop network is the term used for the way a direct connect environment uses the on-premises router to act as the VPC peering point, using VLAN abstractions to route the various subnets.
Reserved Instances (RIs) – a reserved instance is a billing construct where instance resources are reserved, leading to substantial savings. There are two types of RIs there are Standard or Convertible. (not like the car) A Standard RI is purchased and tied to an AZ, whereas a convertible RI is tied to a region. For you VMware folks RIs are like Resource Pools used in vRA you can set the allocated resources for a tenant to consume and they are guaranteed those resources. On Demand instances land in AZs somewhat dependent on resources available, RIs of both types can and do block off resources for your account. We will delve into this deeper in another blog.
Amazon Machine Images (AMIs) – <noun pronounced A-Meez or AM-eez depending on what part of the country you are from> – These are like your VMware templates, they are base OS images or partner provided machine images like OVAs that you can easily deploy in your VPC.
Elastic Load Balancers (ELBs) – ELBs are used for load balancing applications and instances both inter and intra AZ.
Tags – This one is interesting tags are used in various ways both as instance names and as a way to indicate an instance is part of a group of machines performing a set function. Use tags often you can have a max of 50 tags per resource. The best practice is to tag for simplicity
Roles – roles assume policies
Policies – provide granular permissions to resources
Identity Access Manager (IAM) – This is the crux of the operation creating user and service accounts, managing policy and role access and securing resources. Root account, Federation and Multi-Factor Authentication are all managed via IAM.
Multi-Factor Authentication (MFA) – It’s not but it should be mandatory for root accounts and really any account that’s accessing the AWS console.
This should be a good start I am sure I will loop back and update this periodically as new services or terms come up and need explaining.


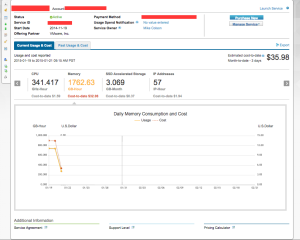
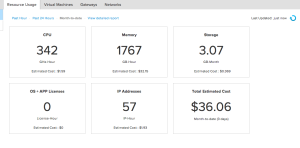
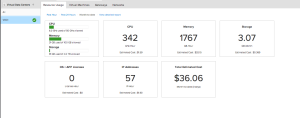
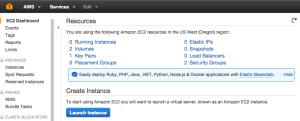 You can also drill into individual VPC’s to see their specific cost modeling and usage.
You can also drill into individual VPC’s to see their specific cost modeling and usage.