As promised I will now talk about containers vs micro services. UGH ok where to start … Maybe it’s best if I do this in a dialog I recently had. Customer will be C I will be M. Also incase you haven’t read these sorts of things before <> will indicate internal dialog or though in my brains.
C: “ I am looking at Docker or VMware Photon to manage a bunch of web sites deployed in containers.”
M: <Ok I thought.>
C: “The web sites are currently deployed and we want to migrate them off of a unix server that they are sitting on today.”
M: <Hmmm, ok weird but if they rebuilt them …. >
C: “We just need to get them off the box as is today”
M: <But but that’s not what containers ….. ok. >
Here is my problem I am no good at keeping my mouth shut, like no good at all. I keep repeating to myself, Mike just stay quiet and people won’t think you are an ass. But then I open my mouth and well words fall out. 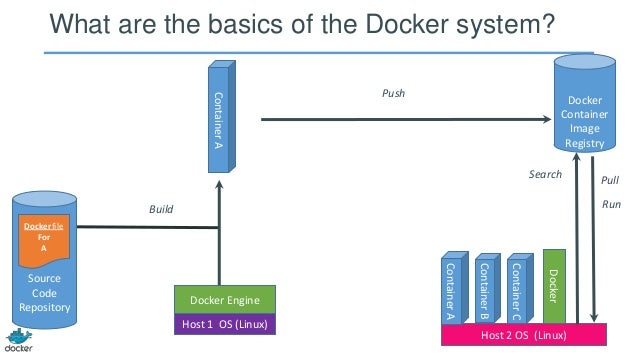
M: “No sir, that’s a bad use case for Docker or Photon. You see a container is great if you have an application and want to deploy multiples of it. Scale it out, not so great for existing web services, better if you were to rebuild them and need multiple instances”
C: “Right like we have a lot of web sites, plus containers provide isolation and security.”
I could actually feel my eye twitch a little here. You know like the eye lid and the side of my face. Maybe it was a stroke?

M: “No see if you wanted to move them off of their existing hardware, just a straight virtual migration would be good, or you could use a code release software to layer them onto a micro kernel vm. But for what it sounds like you want, containers would be tricky. You see you need to have a host OS arguments here can be made that, that OS can be virtualized or bare metal. Then you have your container technology, your containers, and some orchestration methodology that maps them together. Containers are way different than the virtual environments you are used to managing and deploying today.”
Ok so at this point the conversation trailed into other things, and I won’t bore you with those I am just going to use my imagination to finish this conversation as I believe it would have gone.
C: “Yes but I was saw at VMworld …”
M: “I am not saying that container strategies are wrong, nor that you shouldn’t invest time and energy into having one. Quite the contrary I think there is a place for containers in environments where application management is difficult and the concept of micro services isn’t possible to adopt. But containers while they do provide another layer of abstraction are not natively more secure. In fact containers provide the app dev or owner all the more control over the application they are packaging and deploying.”
C: “But it’s isolated so that means any vulnerabilities they expose in their container can’t impact my infrastructure.”
M: “Have you ever watched Lassie?”
C: “What?”
M: “Lassie you know the dog that always saved people?”
C: “ … Yes”
 M: “At the end of ever episode Timmy, the boy who owned Lassie learned a lesson in the form of a speech that his dad gave him. South Park uses this in all of their episodes where Stan and Kyle reminisce on the lessons of the episode. We call this a ‘SoYaSeeTimmy’. The point is no one learns the lesson while they are going through the adventure, they learn after the fact.”
M: “At the end of ever episode Timmy, the boy who owned Lassie learned a lesson in the form of a speech that his dad gave him. South Park uses this in all of their episodes where Stan and Kyle reminisce on the lessons of the episode. We call this a ‘SoYaSeeTimmy’. The point is no one learns the lesson while they are going through the adventure, they learn after the fact.”
C: <blank stare>
M: “So you see Timmy, mind if I call you Timmy? Good. So you see Timmy, you surely can run your web services in a container, or believe your container is actually not going to impact or open you up to security vulnerabilities, but just like when you fell down the well while trying to walk across a board like a balance beam, and Lassie came a running barking, and spinning in circles to get me to follow her back to you, you will learn that just because you can doesn’t mean you should.”
If I am incorrect or you feel differently let’s discuss it, I am still learning and could use a conversation on this that isn’t in my head. 🙂

 Many of you have heard me or someone else expound on the Platforms of Applications that IDC laid out P1 through P3 apps, and the analogy of P2 & P3 apps being like pets and livestock. If not here is a quick synopsis (for those of you who are familiar please read ahead):
Many of you have heard me or someone else expound on the Platforms of Applications that IDC laid out P1 through P3 apps, and the analogy of P2 & P3 apps being like pets and livestock. If not here is a quick synopsis (for those of you who are familiar please read ahead): Platform 2 applications are the many of the X86 apps we run today, SharePoint, Exchange, SQL Server, Oracle, etc. These applications all require care and feeding, but if we want more from them then we need to grow them vertically. Meaning more app servers running the same applications and clusters or split resources. These sorts of application trade offs are fine and expected, and in fact the app owners tend to care for the apps as though they are part of their family, polishing the server bezels and spouting things like “Precious!” They are also the ones who are quick to blame infrastructure teams for their apps failings when service interruptions occur because redundancy is tied directly to the environment it sits on.
Platform 2 applications are the many of the X86 apps we run today, SharePoint, Exchange, SQL Server, Oracle, etc. These applications all require care and feeding, but if we want more from them then we need to grow them vertically. Meaning more app servers running the same applications and clusters or split resources. These sorts of application trade offs are fine and expected, and in fact the app owners tend to care for the apps as though they are part of their family, polishing the server bezels and spouting things like “Precious!” They are also the ones who are quick to blame infrastructure teams for their apps failings when service interruptions occur because redundancy is tied directly to the environment it sits on. more appropriate. Thanks to the recent Ashley Madison hack folks are actually equating sex and security more than ever. Thank goodness for that because security really needs to be viewed in a better light even if it is a red light.
more appropriate. Thanks to the recent Ashley Madison hack folks are actually equating sex and security more than ever. Thank goodness for that because security really needs to be viewed in a better light even if it is a red light. password an idiot would have on their luggage.
password an idiot would have on their luggage.